Security
StackOps works exclusively with STS temporary credentials.
Identity and Access Management
Access Role with Identity
Access to StackOps is controlled by an IAM Role that is created during installation (ie creating the StackOps CloudFormation stack). The created role has:
- a principal element based on the
AuthorizedUserArnsstack parameter; and - allows
AuthorizedUserArnsto assume the access role; and - allows execution of the StackOps Amazon API Gateway WebSocket.
To change who can access StackOps, update the StackOps CloudFormation stack by changing the AuthorizedUserArns
parameter.
AWS IAM Identity Center roles are a good choice for controlling access. Obtain your user role by:
- Log into AWS IAM Identity Center
- Select Accounts tab
- Decide which AWS Account you want to use for temporary credentials
- Open AWS Console
- Open CloudShell and execute
aws sts get-caller-identity - Copy the Arn
Log In
Log in to StackOps by:
- Log into AWS IAM Identity Center
- Select Accounts tab
- Select AWS Account corresponding to your
AuthorizedUserArnsprincipal (from 3 above) - Click Access Keys
- Copy Option 2: Add a profile to your AWS credentials file temporary credentials
- Opening your browser with the StackOps url (Outputs tab of the CloudFormation stack)
- Paste your temporary credentials
Deployment Roles
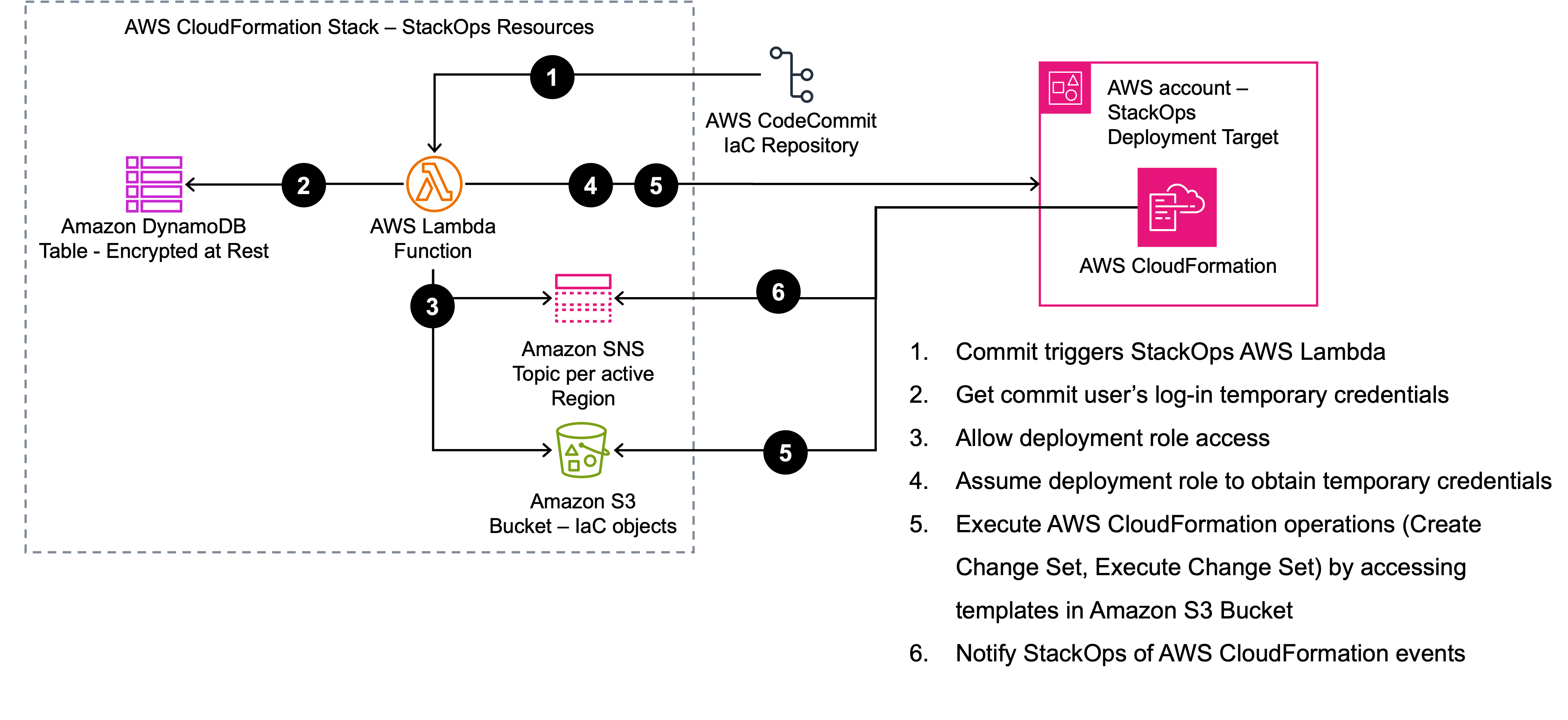
StackOps has been designed to allow logged-in users to manage CloudFormation stacks using the roles specified in deployment files.
Ensure users who can log into StackOps are able to assume all the roles contained in deployment files.
Install additional StackOps instances to separate resource management responsibilities.
Authorization Explanation
This section is for information purposes only.
Steps to authorize a user when they log in.

Steps to authorize AWS CloudFormation operations.